Chapter 16 and 17 Exam Review 2015 Statistics
Introduction to Networks ( Version 7.00) – Modules sixteen – 17: Building and Securing a Pocket-size Network Exam
1. Which component is designed to protect confronting unauthorized communications to and from a estimator?
- security center
- port scanner
- antimalware
- antivirus
- firewall
2. Which command volition block login attempts on RouterA for a catamenia of 30 seconds if there are 2 failed login attempts within ten seconds?
- RouterA(config)# login block-for 10 attempts 2 within 30
- RouterA(config)# login block-for 30 attempts 2 within 10
- RouterA(config)# login block-for two attempts xxx within x
- RouterA(config)# login cake-for 30 attempts 10 within two
3. What is the purpose of the network security accounting function?
- to require users to testify who they are
- to determine which resources a user can access
- to keep track of the actions of a user
- to provide claiming and response questions
four. What blazon of assail may involve the employ of tools such as nslookup and fping?
- admission attack
- reconnaissance attack
- deprival of service attack
- worm attack
5. Lucifer each weakness with an example. (Not all options are used.)
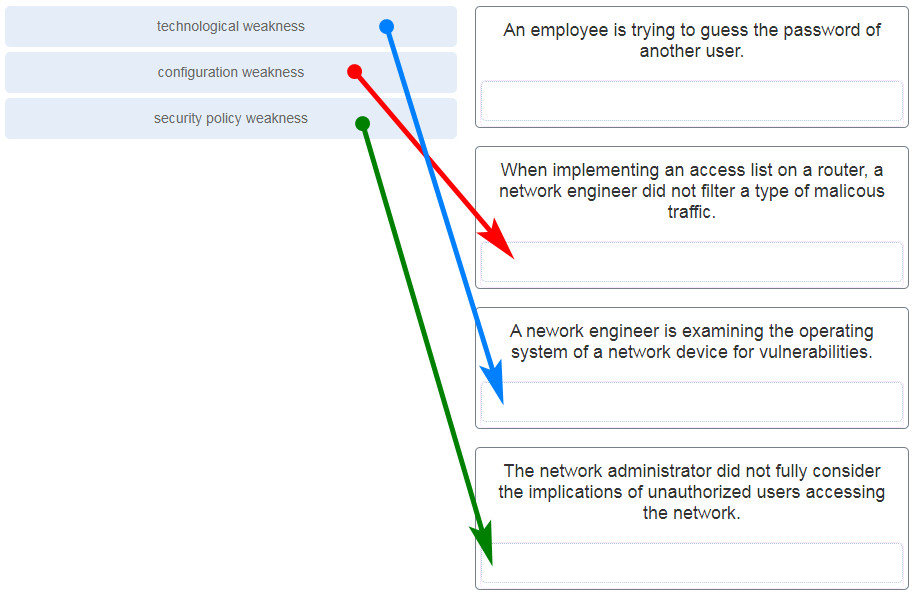
6. Match the type of information security threat to the scenario. (Not all options are used.)
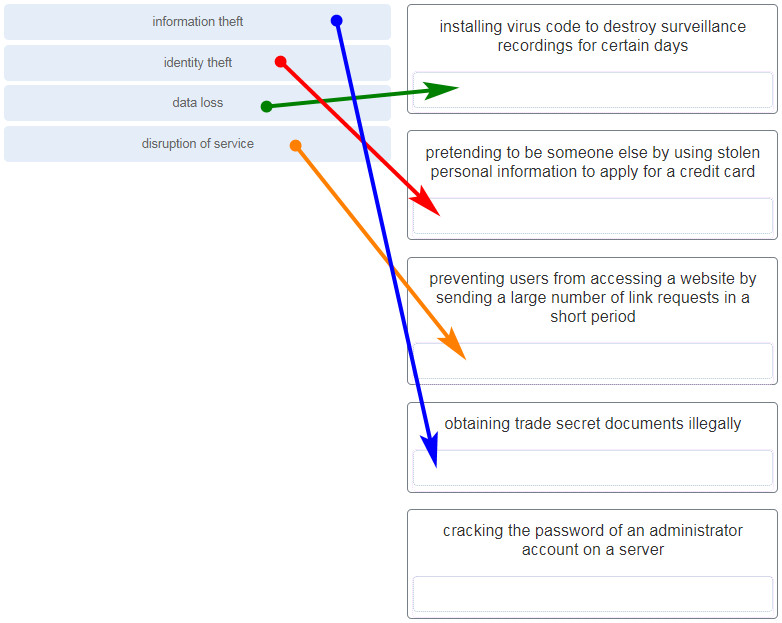
seven. Which example of malicious code would exist classified as a Trojan horse?
- malware that was written to look like a video game
- malware that requires manual user intervention to spread between systems
- malware that attaches itself to a legitimate programme and spreads to other programs when launched
- malware that tin can automatically spread from ane organisation to another past exploiting a vulnerability in the target
eight. What is the difference between a virus and a worm?
- Viruses self-replicate but worms practice not.
- Worms cocky-replicate but viruses do non.
- Worms crave a host file just viruses practise not.
- Viruses hide in legitimate programs but worms do not.
9. Which attack involves a compromise of data that occurs between two end points?
- denial-of-service
- man-in-the-middle attack
- extraction of security parameters
- username enumeration
ten. Which type of assault involves an adversary attempting to gather information about a network to identify vulnerabilities?
- reconnaissance
- DoS
- lexicon
- man-in-the-middle
eleven. Match the description to the type of firewall filtering. (Not all options are used.)
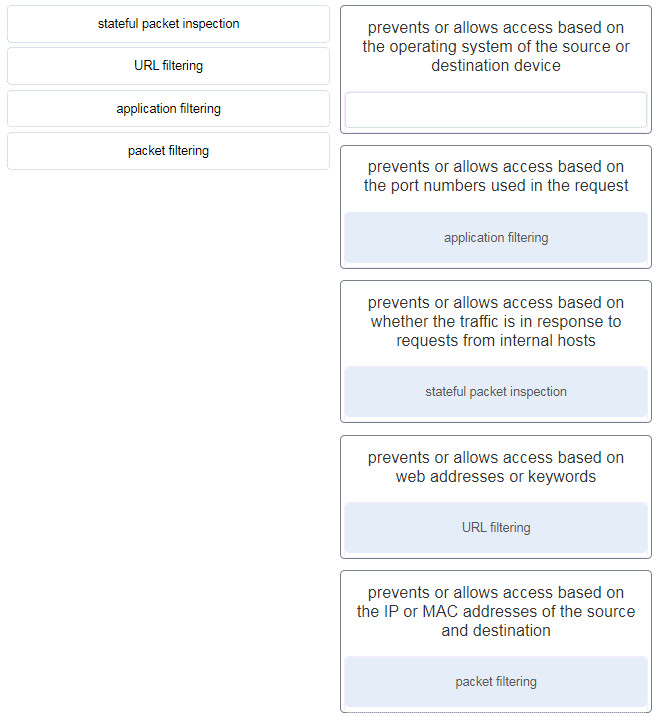
12. What is the purpose of the network security authentication function?
- to require users to evidence who they are
- to determine which resource a user tin access
- to keep track of the deportment of a user
- to provide claiming and response questions
13. Which firewall feature is used to ensure that packets coming into a network are legitimate responses to requests initiated from internal hosts?
- stateful packet inspection
- URL filtering
- awarding filtering
- packet filtering
14. When applied to a router, which control would aid mitigate brute-force password attacks against the router?
- exec-timeout thirty
- service password-encryption
- banner motd $Max failed logins = five$
- login block-for threescore attempts 5 within 60
15. Identify the steps needed to configure a switch for SSH. The answer club does non affair. (Non all options are used.)
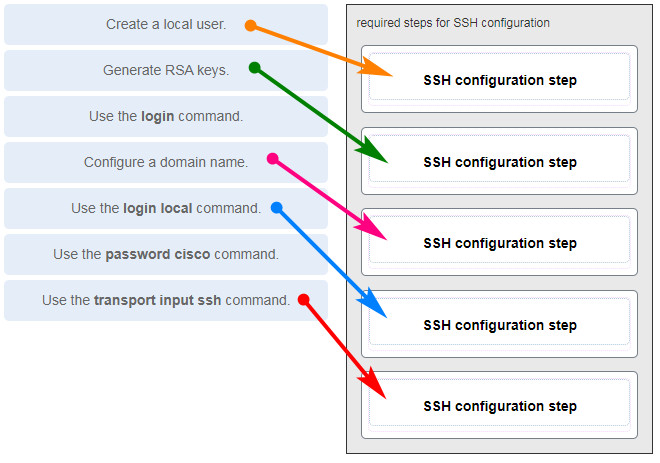
16. What characteristic of SSH makes it more secure than Telnet for a device management connection?
- confidentiality with IPsec
- stronger countersign requirement
- random i-time port connection
- login information and data encryption
17. What is the advantage of using SSH over Telnet?
- SSH is easier to employ.
- SSH operates faster than Telnet.
- SSH provides secure communications to access hosts.
- SSH supports authentication for a connectedness asking.
18. What is the office of an IPS?
- detecting and blocking of attacks in real time
- connecting global threat information to Cisco network security devices
- authenticating and validating traffic
- filtering of nefarious websites
19. A user is redesigning a network for a small company and wants to ensure security at a reasonable cost. The user deploys a new application-enlightened firewall with intrusion detection capabilities on the Internet service provider connexion. The user installs a 2nd firewall to separate the company network from the public network. Additionally, the user installs an IPS on the internal network of the company. What approach is the user implementing?
- attack based
- risk based
- structured
- layered
20. What is an accurate clarification of redundancy?
- configuring a router with a consummate MAC address database to ensure that all frames tin can be forwarded to the correct destination
- configuring a switch with proper security to ensure that all traffic forwarded through an interface is filtered
- designing a network to utilise multiple virtual devices to ensure that all traffic uses the best path through the internetwork
- designing a network to utilise multiple paths betwixt switches to ensure in that location is no single point of failure
21. A network administrator is upgrading a pocket-sized concern network to requite high priority to real-time applications traffic. What ii types of network services is the network administrator trying to adjust? (Choose two.)
- vocalism
- video
- instant messaging
- FTP
- SNMP
22. What is the purpose of a small company using a protocol analyzer utility to capture network traffic on the network segments where the visitor is considering a network upgrade?
- to place the source and destination of local network traffic
- to capture the Internet connection bandwidth requirement
- to document and clarify network traffic requirements on each network segment
- to establish a baseline for security assay after the network is upgraded
23. Refer to the exhibit. An administrator is testing connectivity to a remote device with the IP accost 10.1.i.ane. What does the output of this command signal?
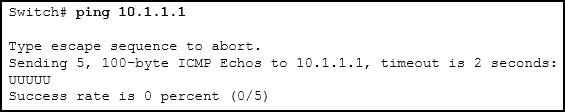
- Connectivity to the remote device was successful.
- A router along the path did not have a route to the destination.
- A ping packet is being blocked by a security device forth the path.
- The connection timed out while waiting for a reply from the remote device.
24. Which method is used to send a ping message specifying the source address for the ping?
- Outcome the ping command from inside interface configuration mode.
- Issue the ping command without specifying a destination IP address.
- Consequence the ping command without extended commands.
- Result the ping control after shutting down un-needed interfaces.
25. A network engineer is analyzing reports from a recently performed network baseline. Which state of affairs would depict a possible latency result?
- a alter in the bandwidth according to the evidence interfaces output
- a next-hop timeout from a traceroute
- an increase in host-to-host ping response times
- a modify in the amount of RAM according to the show version output
26. Which statement is true near Cisco IOS ping indicators?
- '!' indicates that the ping was unsuccessful and that the device may have issues finding a DNS server.
- 'U' may indicate that a router along the path did non contain a road to the destination address and that the ping was unsuccessful.
- '.' indicates that the ping was successful but the response fourth dimension was longer than normal.
- A combination of '.' and '!' indicates that a router along the path did non accept a route to the destination accost and responded with an ICMP unreachable message.
27. A user reports a lack of network connectivity. The technician takes command of the user automobile and attempts to ping other computers on the network and these pings fail. The technician pings the default gateway and that also fails. What can exist determined for sure by the results of these tests?
- The NIC in the PC is bad.
- The TCP/IP protocol is not enabled.
- The router that is attached to the aforementioned network as the workstation is downward.
- Nothing tin can be determined for sure at this point.
28. A network technician issues the C:\> tracert -6 www.cisco.com command on a Windows PC. What is the purpose of the -6 command option?
- It forces the trace to use IPv6.
- Information technology limits the trace to merely six hops.
- It sets a 6 milliseconds timeout for each replay.
- It sends 6 probes within each TTL time catamenia.
29. Why would a network administrator employ the tracert utility?
- to make up one's mind the active TCP connections on a PC
- to cheque information about a DNS name in the DNS server
- to identify where a packet was lost or delayed on a network
- to display the IP accost, default gateway, and DNS server address for a PC
30. A ping fails when performed from router R1 to directly connected router R2. The network administrator then gain to issue the show cdp neighbors command. Why would the network administrator event this control if the ping failed betwixt the two routers?
- The network administrator suspects a virus considering the ping command did not work.
- The network ambassador wants to verify Layer ii connectivity.
- The network administrator wants to verify the IP address configured on router R2.
- The network administrator wants to determine if connectivity can be established from a non-directly continued network.
31. A network engineer is troubleshooting connectivity bug among interconnected Cisco routers and switches. Which command should the engineer use to discover the IP address information, host name, and IOS version of neighboring network devices?
- show version
- prove ip road
- show interfaces
- show cdp neighbors item
32. What information about a Cisco router tin be verified using the testify version control?
- the routing protocol version that is enabled
- the value of the configuration register
- the operational condition of serial interfaces
- the administrative distance used to reach networks
33. Which command should be used on a Cisco router or switch to allow log letters to be displayed on remotely connected sessions using Telnet or SSH?
- debug all
- logging synchronous
- prove running-config
- terminal monitor
34. Which control can an administrator result on a Cisco router to send debug messages to the vty lines?
- concluding monitor
- logging console
- logging buffered
- logging synchronous
35. By following a structured troubleshooting arroyo, a network ambassador identified a network issue later on a conversation with the user. What is the next footstep that the administrator should take?
- Verify total system functionality.
- Test the theory to decide cause.
- Establish a theory of probable causes.
- Institute a programme of action to resolve the issue.
36. Users are complaining that they are unable to browse sure websites on the Net. An administrator can successfully ping a web server via its IP address, but cannot browse to the domain proper noun of the website. Which troubleshooting tool would be most useful in determining where the trouble is?
- netstat
- tracert
- nslookup
- ipconfig
37. An employee complains that a Windows PC cannot connect to the Cyberspace. A network technician issues the ipconfig control on the PC and is shown an IP accost of 169.254.10.3. Which two conclusions can be fatigued? (Choose two.)
- The PC cannot contact a DHCP server.
- The DNS server address is misconfigured.
- The default gateway address is not configured.
- The PC is configured to obtain an IP address automatically.
- The enterprise network is misconfigured for dynamic routing.
38. Refer to the showroom. Host H3 is having problem communicating with host H1. The network administrator suspects a trouble exists with the H3 workstation and wants to prove that there is no problem with the R2 configuration. What tool could the network administrator employ on router R2 to prove that communication exists to host H1 from the interface on R2, which is the interface that H3 uses when communicating with remote networks?
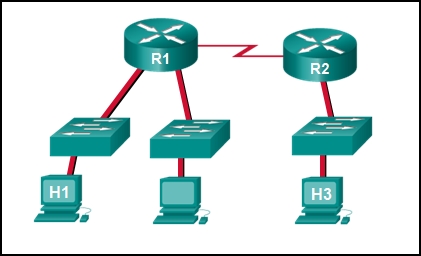
-
traceroute -
show cdp neighbors - Telnet
- an extended ping
39. Refer to the exhibit. Baseline documentation for a small company had ping circular trip time statistics of 36/97/132 between hosts H1 and H3. Today the network administrator checked connectivity by pinging between hosts H1 and H3 that resulted in a round trip time of 1458/2390/6066. What does this indicate to the network administrator?
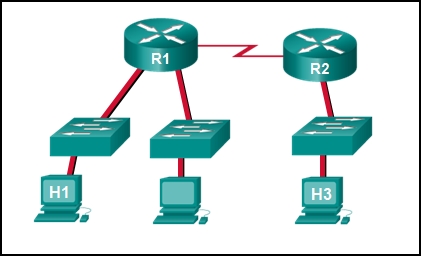
- Connectivity betwixt H1 and H3 is fine.
- H3 is not connected properly to the network.
- Something is causing interference between H1 and R1.
- Performance between the networks is within expected parameters.
- Something is causing a time filibuster between the networks.
xl. Which network service automatically assigns IP addresses to devices on the network?
- DHCP
- Telnet
- DNS
- traceroute
41. Which command can an administrator execute to determine what interface a router volition use to reach remote networks?
- show arp
- show interfaces
- prove ip route
- show protocols
42. On which two interfaces or ports can security be improved past configuring executive timeouts? (Cull 2.)
- Fast Ethernet interfaces
- panel ports
- serial interfaces
- vty ports
- loopback interfaces
43. When configuring SSH on a router to implement secure network direction, a network engineer has issued the login local and transport input ssh line vty commands. What three additional configuration actions take to be performed to consummate the SSH configuration? (Choose three.)
- Set up the user privilege levels.
- Generate the disproportionate RSA keys.
- Configure the correct IP domain name.
- Configure role-based CLI access.
- Create a valid local username and password database.
- Manually enable SSH after the RSA keys are generated.
44. What is considered the most effective way to mitigate a worm set on?
- Change system passwords every 30 days.
- Ensure that all systems accept the most current virus definitions.
- Ensure that AAA is configured in the network.
- Download security updates from the operating system vendor and patch all vulnerable systems.
45. Which statement describes the ping and tracert commands?
- Tracert shows each hop, while ping shows a destination reply only.
- Tracert uses IP addresses; ping does not.
- Both ping and tracert tin show results in a graphical brandish.
- Ping shows whether the manual is successful; tracert does not.
46. A technician is to document the current configurations of all network devices in a higher, including those in off-site buildings. Which protocol would exist best to use to securely access the network devices?
- FTP
- HTTP
- SSH
- Telnet
47. Open the PT Activity. Perform the tasks in the action instructions and then respond the question.
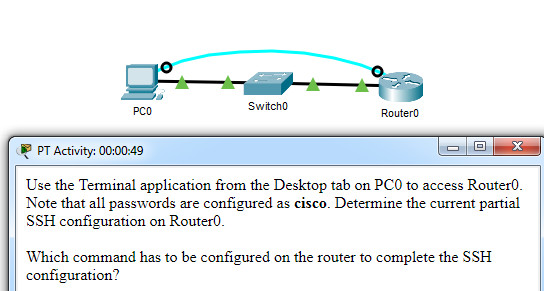
CCNA 1 v7 Modules 16 – 17 Building and Securing a Small Network Exam
Which command has to be configured on the router to consummate the SSH configuration?
- service password-encryption
- ship input ssh
- enable secret form
- ip domain-name cisco.com
48. An administrator decides to apply "WhatAreyouwaiting4" as the password on a newly installed router. Which statement applies to the password pick?
- It is strong because it uses a passphrase.
- It is weak considering information technology is often the default password on new devices.
- It is weak since it uses easily found personal information.
- It is weak since it is a word that is easily found in the dictionary.
49. An ambassador decides to use "pR3s!d7n&0" equally the password on a newly installed router. Which argument applies to the countersign selection?
- It is stiff because it uses a minimum of 10 numbers, messages and special characters.
- It is weak because it is often the default countersign on new devices.
- It is weak since information technology uses easily found personal information.
- It is weak since it is a word that is easily found in the lexicon.
50. An administrator decides to use "v$7*4#033!" as the password on a newly installed router. Which argument applies to the password choice?
- It is strong considering it contains 10 numbers and special characters.
- It is weak because it is often the default countersign on new devices.
- Information technology is weak since it uses easily found personal information.
- It is strong because it uses a minimum of 10 numbers, letters and special characters.
51. An administrator decides to use "pR3s!d7n&0" equally the password on a newly installed router. Which argument applies to the password choice?
- It is stiff because it uses a minimum of 10 numbers, letters and special characters.
- Information technology is weak since it is a give-and-take that is hands found in the dictionary.
- It is strong because information technology uses a passphrase.
- Information technology is strong because it contains 10 numbers and special characters.
52. An administrator decides to use "12345678!" as the password on a newly installed router. Which statement applies to the password choice?
- It is weak because it uses a serial of numbers or messages.
- It is potent because it uses a passphrase.
- It is weak since it is a word that is easily found in the dictionary.
- It is strong because it uses a minimum of 10 numbers, letters and special characters.
53. An administrator decides to use "admin" as the password on a newly installed router. Which argument applies to the countersign option?
- It is weak because information technology is frequently the default countersign on new devices.
- It is strong considering it uses a passphrase.
- It is strong because information technology uses a minimum of 10 numbers, messages and special characters.
- It is stiff considering information technology contains ten numbers and special characters.
54. An administrator decides to apply "Feb121978" every bit the password on a newly installed router. Which statement applies to the countersign option?
- Information technology is weak because it uses hands institute personal information.
- It is potent because it uses a passphrase.
- Information technology is weak since it is a word that is easily found in the lexicon.
- It is potent because information technology uses a minimum of 10 numbers, letters and special characters.
55. An administrator decides to use "countersign" as the password on a newly installed router. Which statement applies to the password pick?
- It is weak considering it is a commonly used countersign.
- It is weak since information technology is a give-and-take that is easily found in the dictionary.
- It is strong considering it uses a passphrase.
- It is potent because it uses a minimum of 10 numbers, messages and special characters.
56. An ambassador decides to apply "RobErT" as the password on a newly installed router. Which statement applies to the password choice?
- It is weak since it uses easily found personal information.
- It is stiff because it uses a passphrase.
- It is strong because information technology uses a minimum of 10 numbers, letters and special characters.
- Information technology is strong because it contains 10 numbers and special characters.
57. An administrator decides to utilize "Elizabeth" as the countersign on a newly installed router. Which statement applies to the password selection?
- It is weak considering it uses easily found personal data.
- It is stiff because it uses a passphrase.
- It is weak since it is a give-and-take that is easily constitute in the lexicon.
- It is strong because information technology uses a minimum of ten numbers, messages and special characters.
Rules for stiff passwords:
* minimum of viii characters, preferably ten.
* utilize complex combinations of numbers, special characters, and upper and lower case messages.
* avoid repetition, common lexicon words, letter or number sequences.
* avert names of children, relatives, pets, birthdays, or any easily identifiable personal information.
* can be created past misspelling words or replacing vowels with numbers or special characters.
58. A network technician is troubleshooting an issue and needs to verify the IP addresses of all interfaces on a router. What is the best command to use to accomplish the task?
- show ip interface brief
- nslookup
- ipconfig getifaddr en0
- prove ip route
59. Students who are connected to the same switch are having slower than normal response times. The administrator suspects a duplex setting consequence. What is the best command to use to achieve the task?
- bear witness interfaces
- ipconfig getifaddr en0
- re-create running-config startup-config
- show ip nat translations
60. A user wants to know the IP address of the PC. What is the best command to apply to achieve the task?
- ipconfig
- copy running-config startup-config
- testify interfaces
- testify ip nat translations
61. A student wants to relieve a router configuration to NVRAM. What is the best control to utilize to accomplish the task?
- re-create running-config startup-config
- show interfaces
- evidence ip nat translations
- show ip route
62. A support technician needs to know the IP address of the wireless interface on a MAC. What is the best control to use to achieve the task?
- ipconfig getifaddr en0
- copy running-config startup-config
- evidence interfaces
- show ip nat translations
63. A network technician is troubleshooting an consequence and needs to verify all of the IPv6 interface addresses on a router. What is the all-time control to utilise to accomplish the job?
- show ipv6 interface
- show interfaces
- show ip nat translations
- show ip route
64. A teacher is having difficulties connecting his PC to the classroom network. He needs to verify that a default gateway is configured correctly. What is the best command to use to accomplish the chore?
- ipconfig
- re-create running-config startup-config
- show interfaces
- show ip nat translations
65. Only employees connected to IPv6 interfaces are having difficulty connecting to remote networks. The analyst wants to verify that IPv6 routing has been enabled. What is the best control to use to accomplish the chore?
- bear witness running-config
- prove interfaces
- copy running-config startup-config
- show ip nat translations
66. An administrator is troubleshooting connectivity issues and needs to make up one's mind the IP address of a website. What is the best command to employ to achieve the task?
- nslookup
- evidence ipv6 route
- show ipv6 interface
- copy startup-config running-config
67. Simply employees connected to IPv6 interfaces are having difficulty connecting to remote networks. The analyst wants to verify that IPv6 routing has been enabled. What is the best control to utilise to attain the task?
- show running-config
- bear witness ipv6 route
- show ipv6 interface
- re-create startup-config running-config
68. What is a characteristic of UDP?
- UDP datagrams take the aforementioned path and go far in the correct guild at the destination.
- Applications that employ UDP are ever considered unreliable.
- UDP reassembles the received datagrams in the order they were received.
- UDP simply passes data to the network when the destination is prepare to receive the data.
Source: https://itexamanswers.net/ccna-1-v7-modules-16-17-building-and-securing-a-small-network-exam-answers.html
0 Response to "Chapter 16 and 17 Exam Review 2015 Statistics"
Post a Comment